The Latest Check Point News
Product and Solution Information, Press Releases, Announcements
| Notice the unnoticed: Threat Hunting by SandBlast Agent | |
| Posted: Fri Oct 16, 2020 11:13:32 AM | |
|
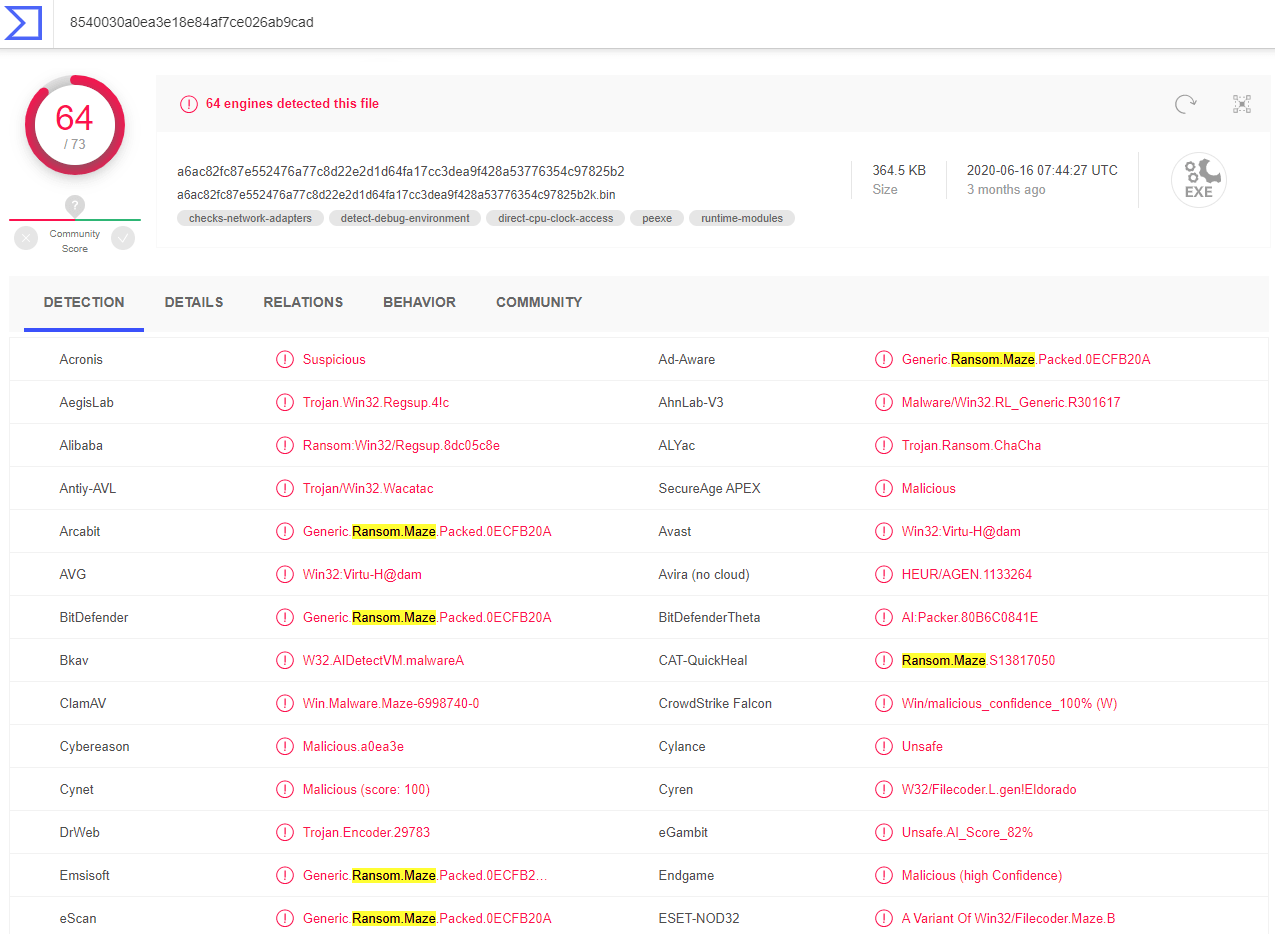
Threat Hunting is a proactive approach for finding and remediating undetected cyber-attacks. It is a process that involves searching for indicators of compromise (IoC), investigating, classifying, and remediate. Threat hunting can be IoC-Driven, in which the hunter investigates an indicator provided by external or internal sources. It can also be hypothesis-driven, in which the hunt begins with an initial hypothesis or question. For example, have we been affected by a recent campaign covered in the news? SandBlast Agentís Threat Hunting solution is a robust platform that helps you hunt and investigate incidents promptly. In the previous chapter we explained how to avoid the damager of the dangerous wave of ransomware attacks. In this blog post, we will demonstrate how to hunt for undetected attacks such as ransomware based on an indicator of compromise and block the attack. Why is Threat Hunting Important?End Point Security experts and analysts proactively hunt and investigate incidents based on indicators provided by threat alliances, open-source intelligence (OSINT), or external intelligence. SandBlast Agentís Threat Hunting solution offers real-time visibility to all indicators collected from all Endpoint devices in the organization. It provides a powerful investigation platform that quickly searches for indicators and provides a list of all appearances across the enterprise hosts, events timeline, and detailed information collected by SandBlast Agent automatic Forensics. Also, the solution offers actionable response options such as quarantine and termination. Maze RansomwareMaze was one of the two top ransomware types in Q3 2020. Maze is not like typical data-encrypting ransomware. Maze not only spreads across a network, infecting and encrypting every computer in its path, it also exfiltrates the data to the attackersí servers where the hacker holds it for ransom. If the victim doesnít pay the ransom, the attackers publish the files online. The FBI privately warned businesses in December of an increase in Maze-related ransomware incidents. Since the warning, several major companies have been hit by Maze, including cyber insurer Chubb, accounting giant MNP, a law firm, an oil company, US military missile contractor, the business services giant Conduent and many more. Letís Start Hunting!The Maza Ransomware hit the headlines a couple of weeks ago when the Ransomware group has claimed responsibility for attacking Virginiaís Largest School System and interrupting the distanced learning of the Fairfax County Public Schools (FCPS). This news might not concern most Endpoint Security experts, but what about those responsible for securing school systems worldwide? They were probably highly concerned and started hunting for the maze Ransomware indicators in their systems. We will now demonstrate how it to hunt for Maze SandBlast Agentís Threat Hunting solution. Enterprise-Wide Visibility Augmented by Threat IntelligenceWe will start the investigation with a known Maze IoC: 8540030a0ea3e18e84af7ce026ab9cad When looking in VirusTotal, it is clear that this indicator is strongly related to the Maze Ransomware:
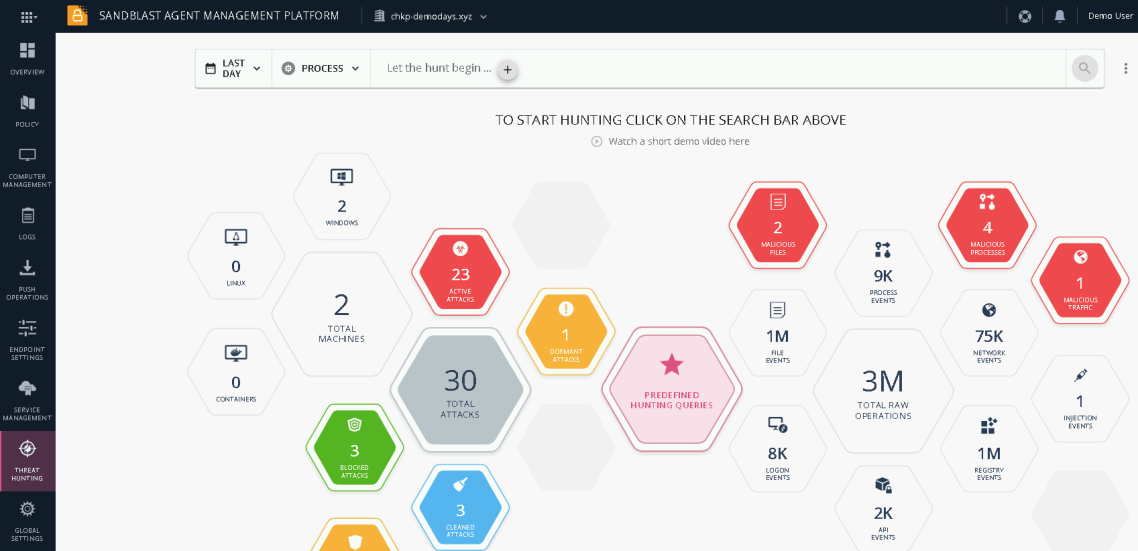
Figure 1 Virus Total Indicator Search Results Now, letís have a look in SandBlast Agentís Threat Hunting Dashboard. We see an overview of the enterprise-wide indicators, collected by SandBlast Agent in all Endpoint devices.
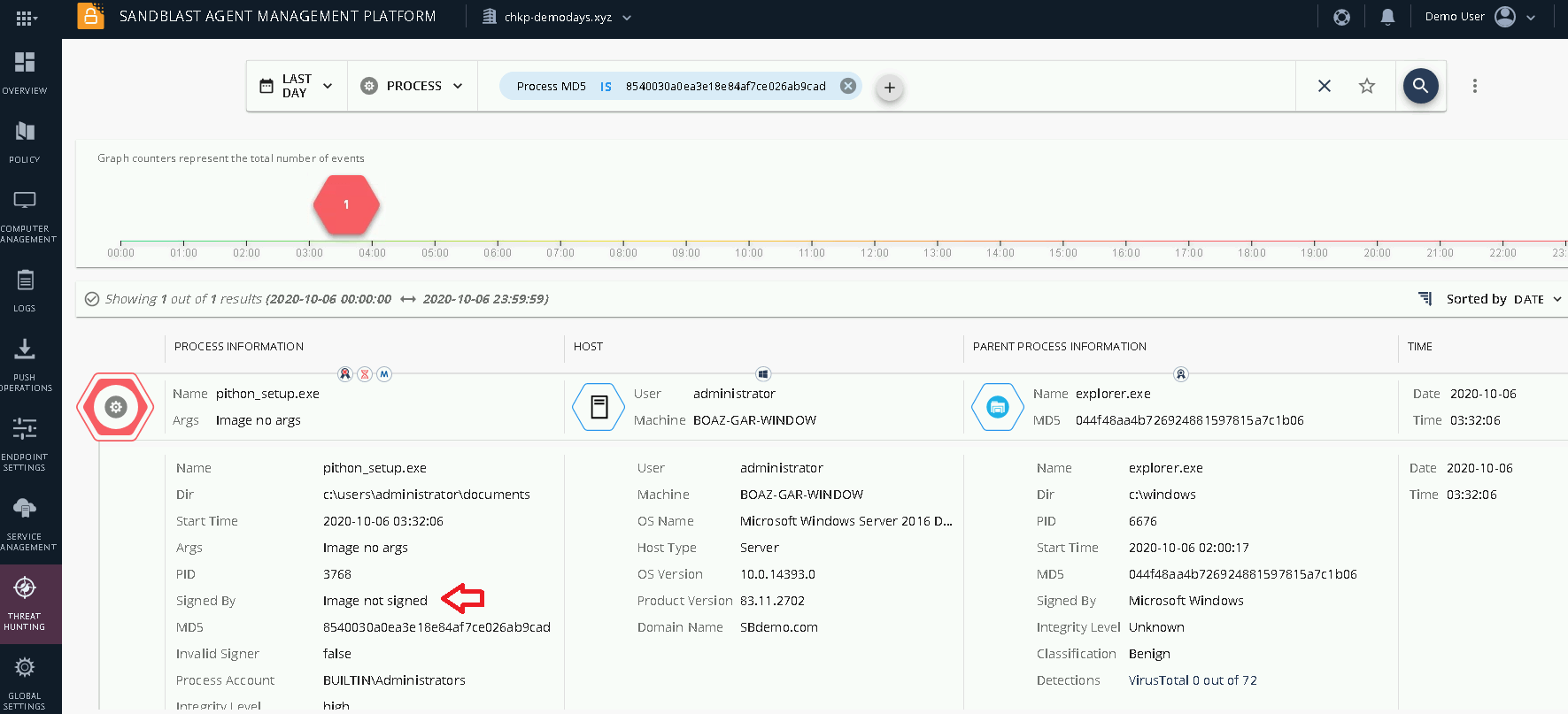
Figure 2 SandBlast Agent Threat Hunting We will use the advanced investigation search tool to search for the indicator weíve got:
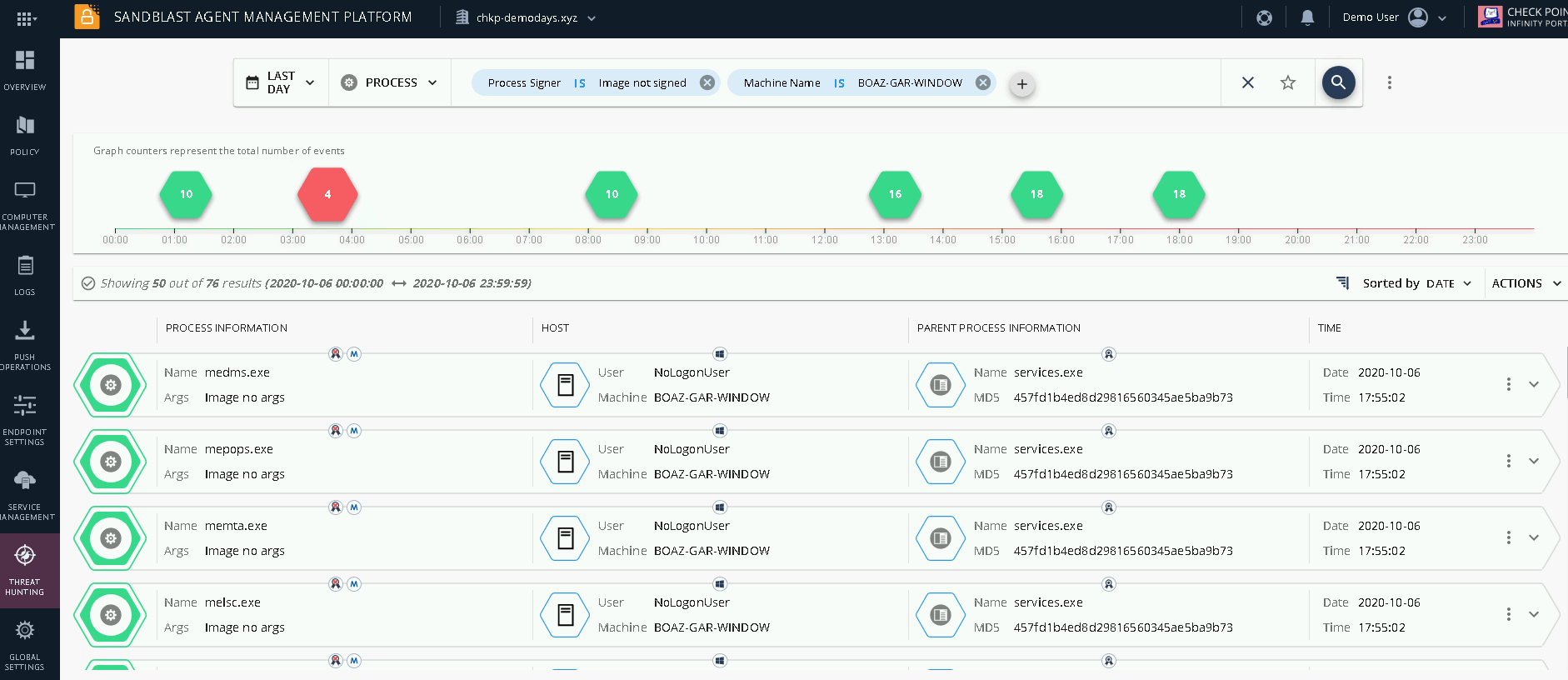
Figure 3 Threat Hunting MD5 Investigation We see that the processís name is pithon_setup.exe, the process is not signed and it was observed only on BOAZ-GAR-WINDOWS machine. Letís add the BOAZ-GAR-WINDOW machine to the query, search for unsigned processes and remove the MD5 to find potential backdoor processes we have yet to discover.
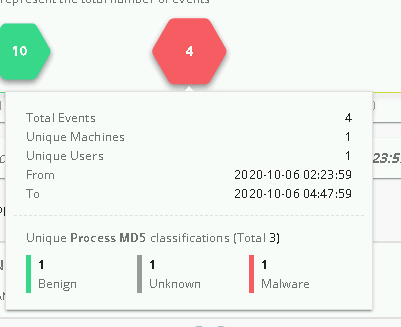
Figure 4 Investigation Continues We see that we have 76 matches. The time-line bar shows us the number of events happening at a certain time. Letís take a closer look:
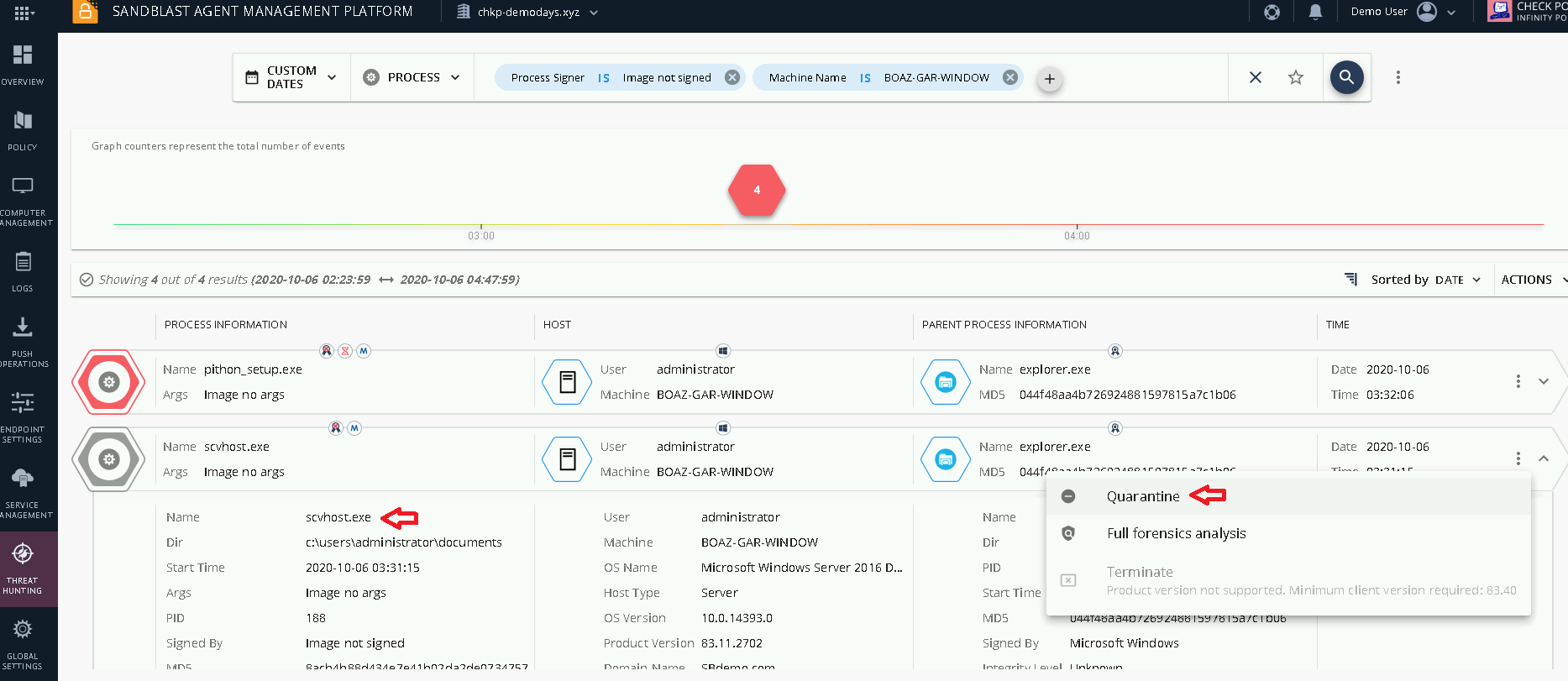
Figure 5 Events Details By clicking on the red hexagon, we exclude trusted events, excellent hunting! We have found the backdoor process that the attacker used to infiltrate the server and execute a Ransomware attack. We can now quarantine the process and continue the investigation to track all possible yet to be activated backdoor processes in the organizationís history.
Figure 6 Backdoor Process Found Enhancing Threat Hunting with globally-shared Threat IntelligenceSandBlast Agent is enriched by Check Point ThreatCloud, the most powerful threat intelligence database. ThreatCloud is continuously updated by advanced predictive intelligence engines, data from hundreds of millions of sensors, cutting-edge research from Check Point Research and external intelligence feed. On a daily basis, ThreatCloud analyzes 10 trillion logs, 86 billion IOCs, 2.6 billion attacks and 3 billion website and files. When a suspicious indicator is detected by SandBlast Agent, it is immediately sent for further analysis by ThreatCloud engines. SandBlast Agentís will then automatically enrich the Forensics Report with ThreatCloud Intelligence. Furthermore, ThreatCloud instantly shares all indicators collected across all endpoint devices, mobile devices, network and cloud engines, with all Check Point customers to make sure that the next occurrence of the attack will be prevented even faster. SummaryIn this chapter, we explained why even organizations equipped with the most comprehensive, state-of-the-art Endpoint Security solution, still need to actively hunt for threats that remained under the radar. We demonstrated how SandBlast Agentís Threat Hunting tool could be used to find unnoticed attacks and remediate them. Using this tool on a regularly, helps you get ready for an unexpected cyber-attack. In the next chapter, we will demonstrate another approach for Threat Hunting, using the MITRE ATT&CK dashboard in SandBlast Agentís Threat Hunting solution. Try SandBlast Agent Threat Hunting tool now. Original Post by Check Point |